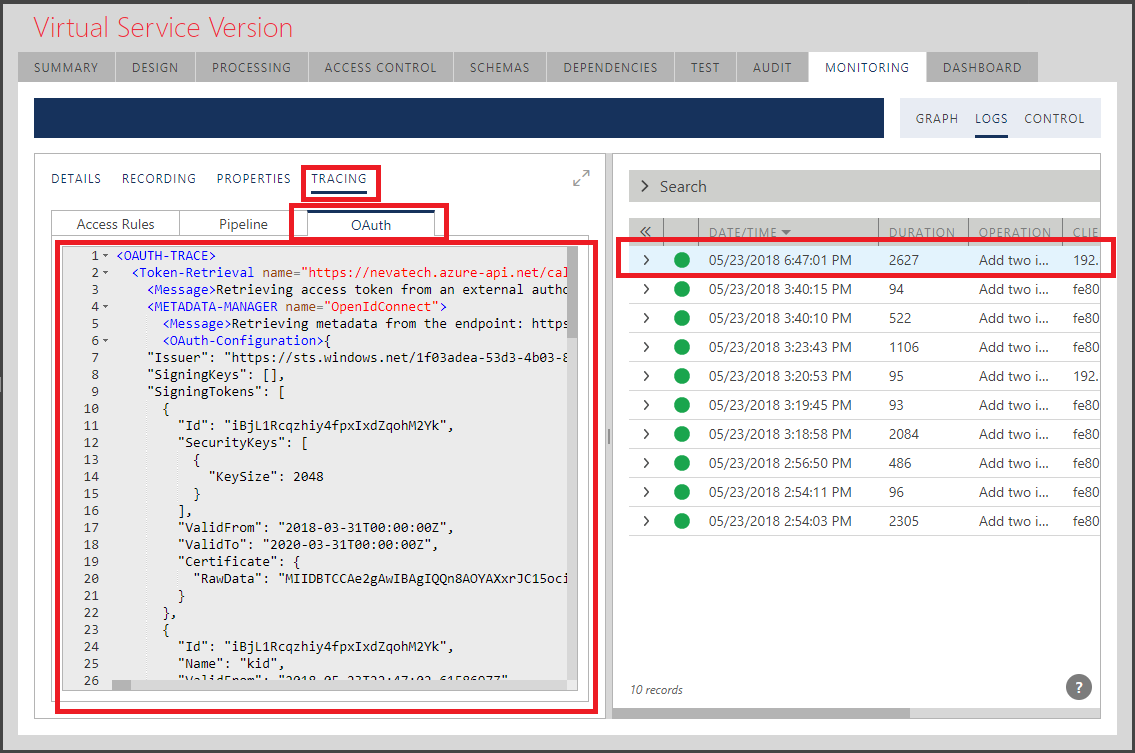
Tracing
Sentinet allows tracing of the execution of the Access Rule Engine, Pipeline execution and OAuth handshakes (see how to enable Tracing in the Tracing chapter). If tracing is enabled, it can be reviewed under the TRACING tab, and then selecting Access Rules, Pipeline and OAuth sub-tabs.
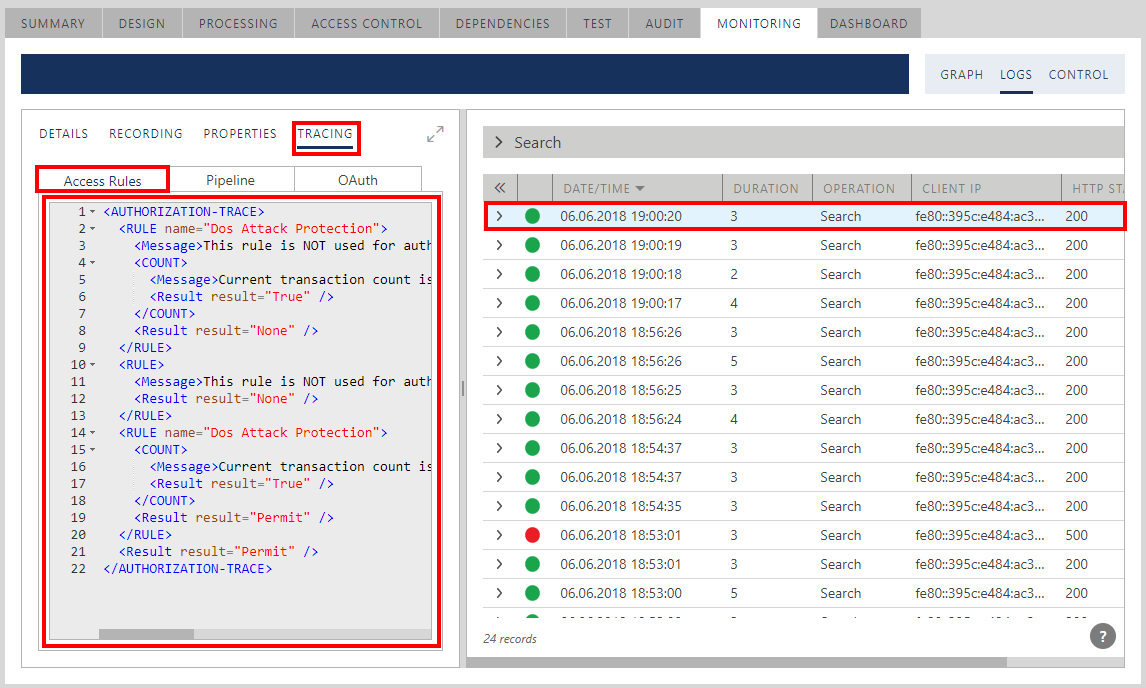
Access Rules Tracing
Access Rules tracing shows an XML document that can be used to read the details of how the Sentinet Authorization Engine executed a selected transaction.
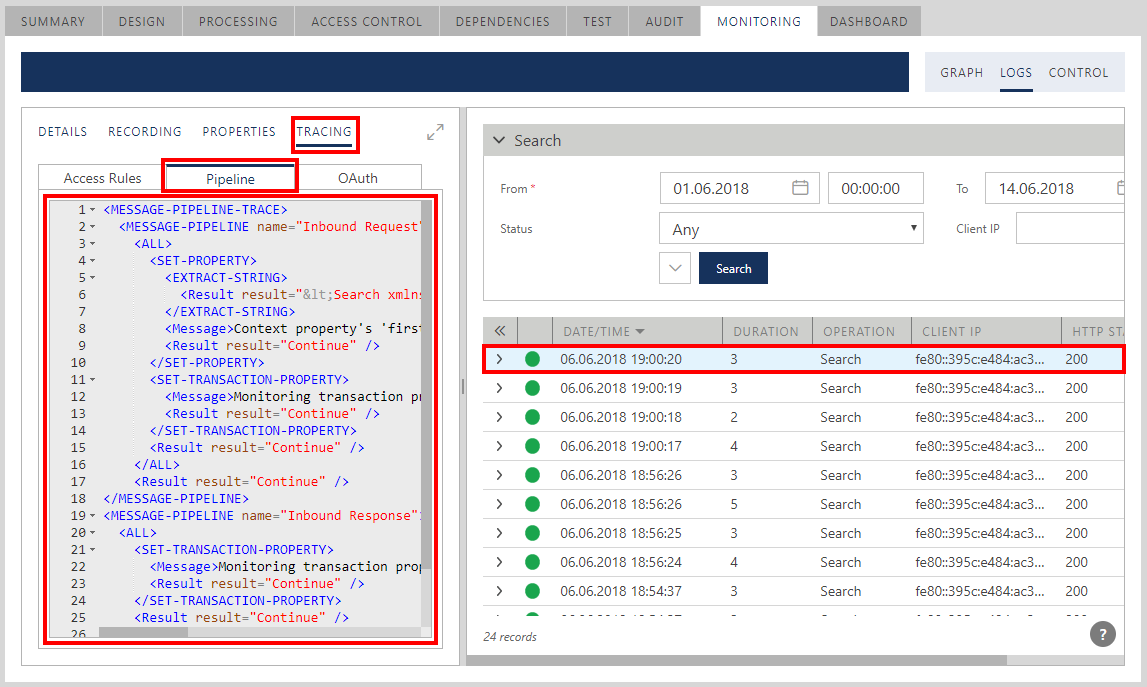
Pipeline Tracing
Pipeline tracing shows XML document that can be used to read details of how Pipeline executed a selected transaction.
OAuth Tracing
OAuth tracing shows an XML document that can be used to read details of how the virtual service handled the OAuth security models including any additional handshakes with external OAuth servers.