X.509 Certificates Management Infrastructure
Sentinet provides a X.509 certificates management infrastructure with two distinct and independent features:
Sentinet can be used as a trusted Certificate Authority that issues other certificates used by Sentinet Nodes, business services and business service consumers.
Sentinet can monitor and alert administrators on all certificates that are used by Sentinet and about to expire.
Certificate Authority
During initial installation and configuration of the Sentinet Repository Web Application, it is configured with a self-signed X.509 certificate that has the capability to issue other X.509 certificates (see the Sentinet Installation Guide on how to generate and configure Sentinet Signing certificate). The use of this Sentinet feature is entirely optional and complementary to the use of well-known and industry standard Certificate Authorities (CAs). At the same time, the feature enables administrators to operate Sentinet in an explicitly trusted X.509 certificates realm, where some or all the certificates used by the business services and consumers are required to be signed by an organization's unique signing certificate. In addition to cost savings associated with issuance of certificates through commercial CAs, developers can also benefit from the immediate issuance of unlimited test certificates for their development and test environments, where issued certificates will be guaranteed to be valid and trusted by Sentinet and its managed services.
There are two distinct processes that can use Sentinet as a Certificate Authority:
The Sentinet Node registration process that always requires an X.509 certificate to be assigned to a Sentinet Node. (See the Sentinet Installation Guide for more details on how to generate and configure Sentinet Nodes with the certificate issued by a Sentinet Repository Application.)
Issuance of an X.509 certificate using the Sentinet Administrative Console for any generic purpose such as using a certificate with business services, virtual services or with consumer applications.
Select the Repository root element, click the CONFIGURATION tab and then the CERTIFICATES sub-tab.
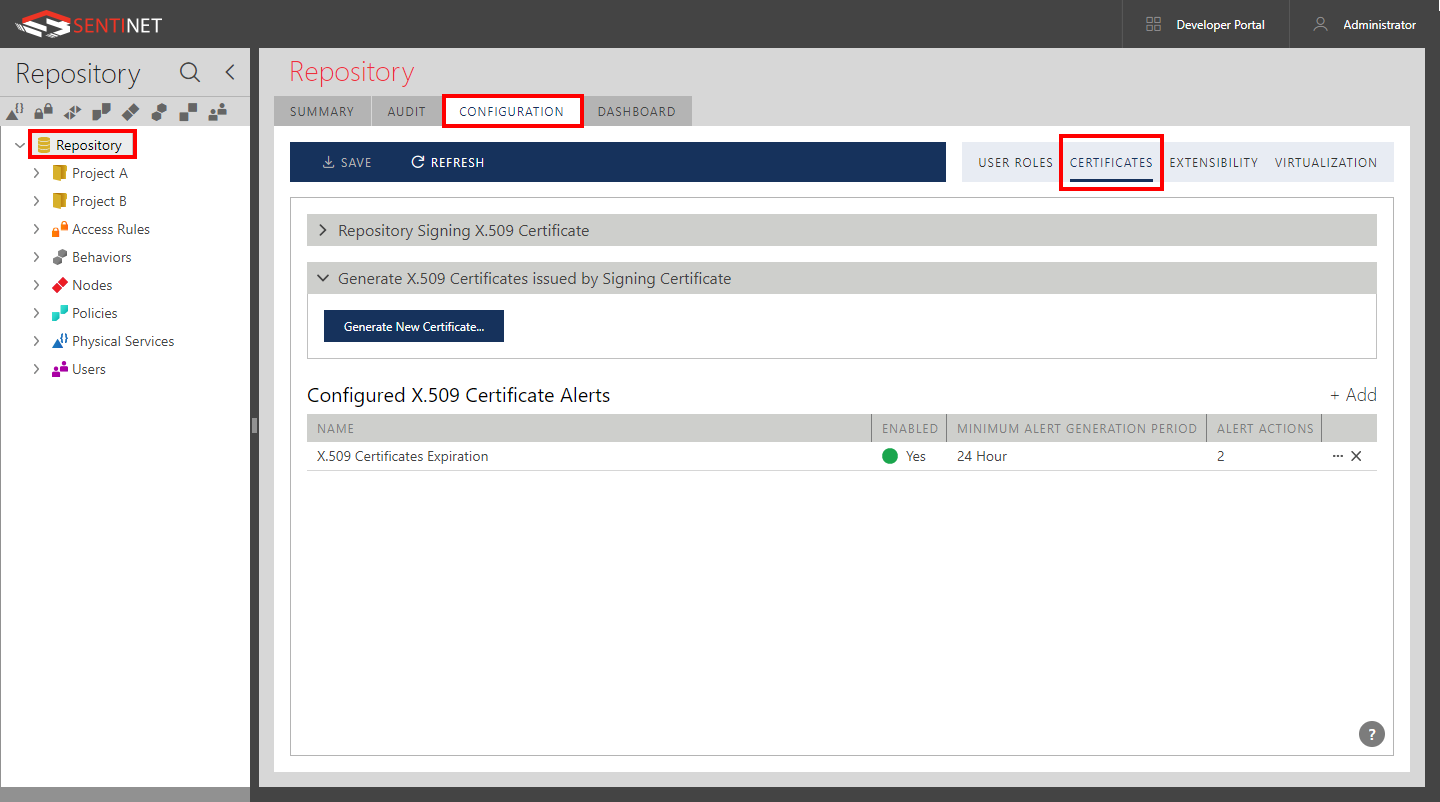
Repository Signing X.509 Certificate
View details of the Repository Signing (CA) certificate. Click the Save button to export the certificate's public part to an external base-64 .CER file. This public certificate can be used by applications requiring a Repository Signing certificate in its trusted chain.
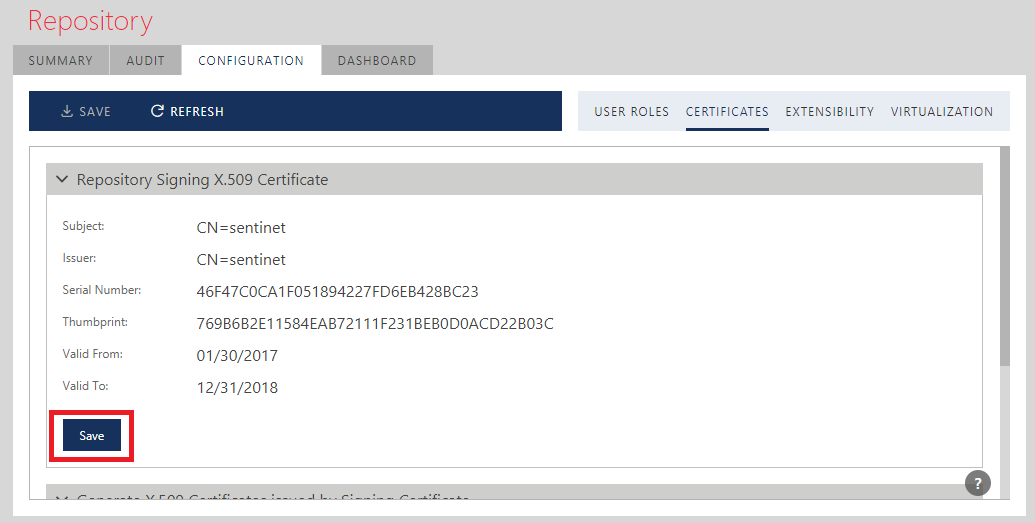
Generate X.509 Certificates
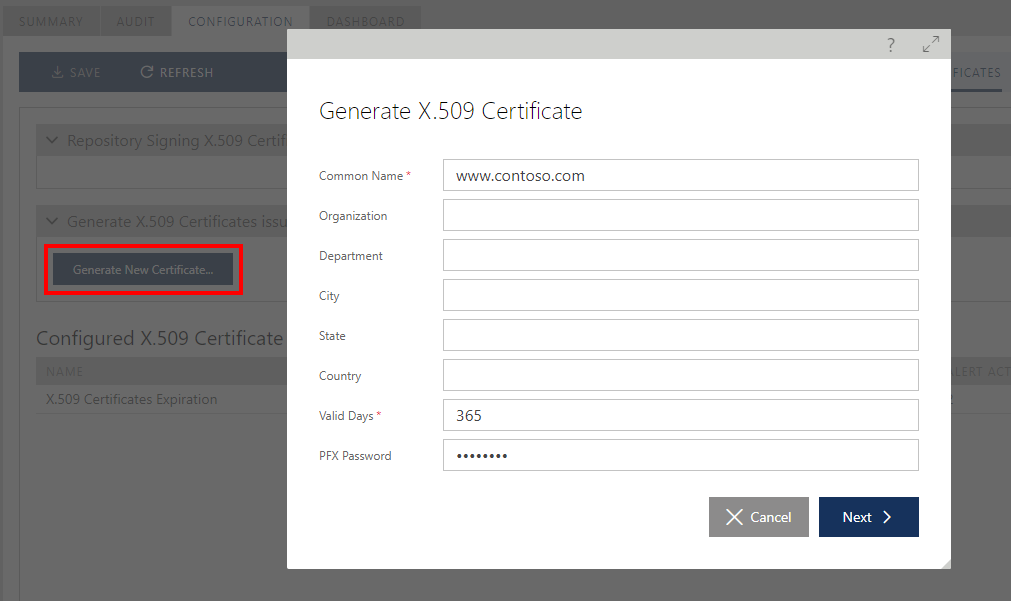
Click the Generate New Certificate button to generate a certificate issued by the Sentinet Repository Application, and provide Certificate Signing Request info and a password for the generated certificate's PFX file, which is a standard certificate file format secured with a password. The generated certificate will be valid from current time until the next Valid Days field value.
The Sentinet Repository Web Application may limit the requested Valid Days value according to the global limit set in the Repository Application web.config file:
<nevatech.vsb.repository>
<security requireHttps="true" httpsRedirectHost=" contoso.com" httpsRedirectPort="-1">
<certificateAuthority keySize="2048" expirationMonths="24">
…
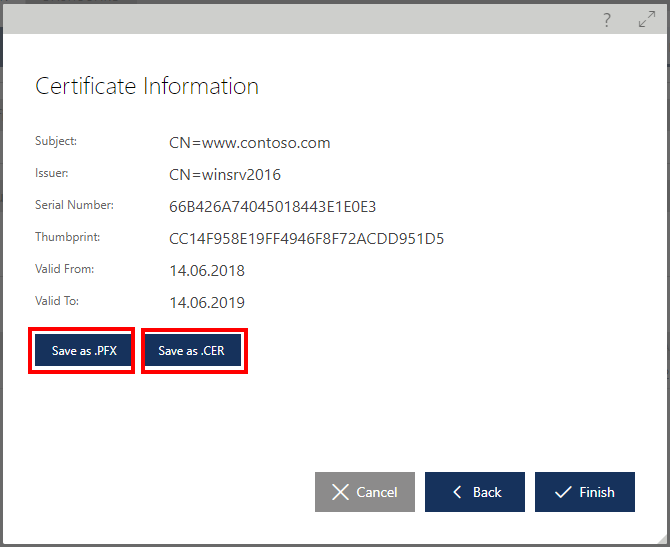
The certificate will be generated by the Repository Web Application and securely delivered to the Sentinet Administrative Console. A Sentinet administrator can save it in an external password-protected PFX file.
Certificates Monitoring and Alerts
X.509 certificates are all subject to expiration, causing invalidation, which may immediately break communication between consumer and service applications. Sentinet provides support for monitoring and alerting on certificates that are about to expire to avoid an operational outage. By default, Sentinet configures one alert with two alert actions. The alert mechanics are the same as described in the Alerts chapter in this guide. The Certificates Expiration Alert has two alert-specific properties, Check active certificates only and Alert when certificate expires in less than days:
Check active certificates only flag. By default, this flag is set to Yes, which means certificates used with inactive services will not be monitored and alerted on.
Alert when certificate expires in less than. This field, measured in days (by default 30), instructs Sentinet to start generating certificate expiration alerts for expired certificates, and for those that will expire in less than the specified number of days.
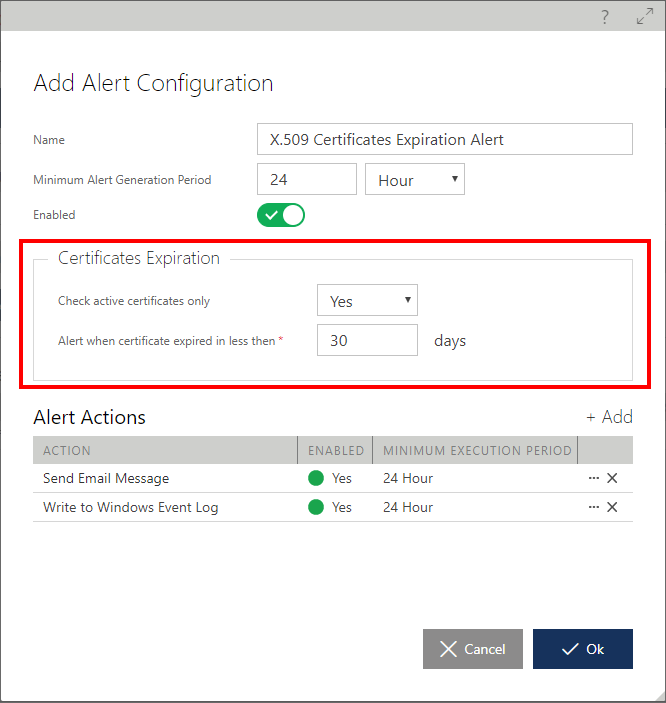
Figure. X.509 Certificate Expiration Alert Sentinet administrators can add new certificate expiration alerts and alert actions, as well as modify or delete an existing default alert and its alert actions.