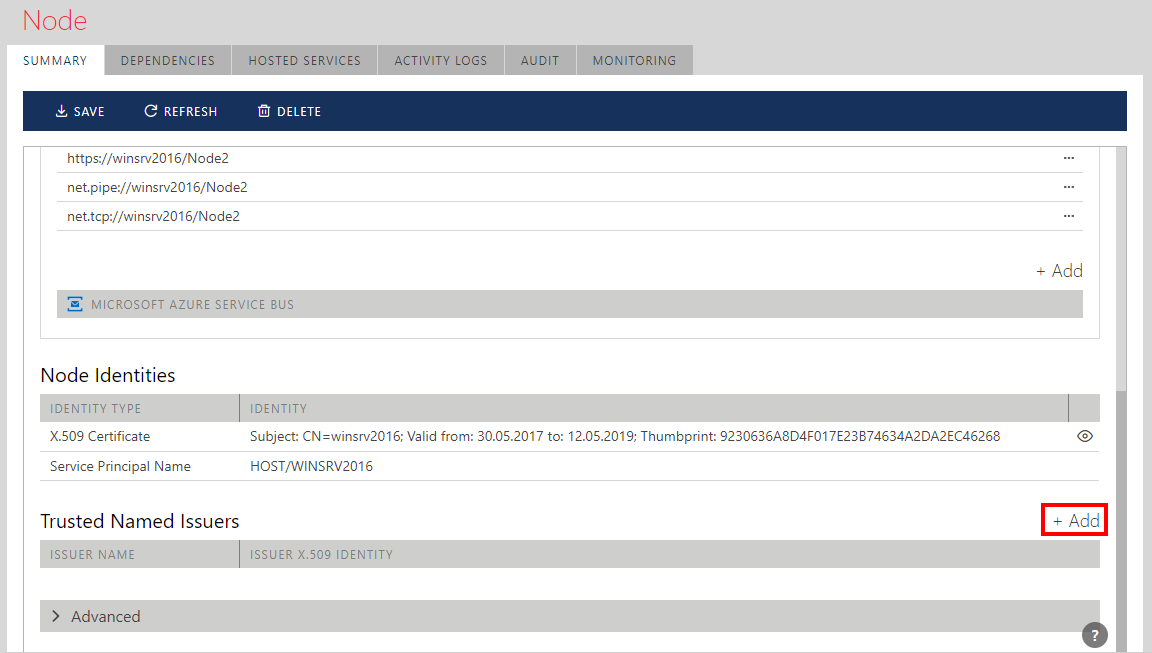
Trusted Named Issuers
Trusted Names Issuers is the list of X.509 certificates that are used by Sentinet Nodes for two independent scenarios, Trusted SSL Server Certificates and Configuration of SAML Aliases.
Trusted SSL Server Certificates
When Sentinet Nodes make forward calls to physical services over SSL, Nodes must trust SSL certificates configured with these external physical services. Sentinet Nodes rely on Windows Certificate Stores on the Local Machine where Sentinet is running. Trust for external server SSL certificates is driven by the content of the Trusted Publishers Certificate Store. If SSL server certificate of the physical service is not signed by the trusted Certificate Authority, but must be used as trusted anyway (for example self-signed SSL certificate), then the certificate of this authority (or self-signed certificate if it is) must be added to the Sentinet Node server’s Trusted Publishers Certificate Store. This requires physical access to the Sentinet Node server (for example via remote desktop). To bypass the need for the physical access to the Sentinet Node server, Sentinet Administrative Console allows users to remotely upload specific SSL certificates which must be trusted by the Sentinet Node. Specific SSL certificates which are added to the Trusted Names Issuers list, will be automatically trusted by the Node regardless of the content of Node server’s Trusted Publishers Certificate Store.
Configuration of SAML Aliases
Access to the Sentinet virtual services may be managed by the Access Rules (see Access Rules and Access Control chapters in this guide) that require validation of the security tokens issued by external Trusted Issuers (or Trusted Authorities). For example, an external Security Token Service may generate SAML tokens signed by its token-signing certificate. These SAML tokens are later sent to the Sentinet virtual services by the client applications. A Sentinet Access Rule expression might be configured to validate both token issuer and token claims. By default, SAML token issuers are identified by the thumbprint of their signing certificate. Sentinet Claims Access Rule Expression may be configured with this thumbprint value, but in many cases humanly readable Issuer Name aliases are preferred over the digital thumbprint values. Windows Identity Foundation provides configuration sections to define named trusted issuers in its <trustedIssuers> section, https://msdn.microsoft.com/en-us/library/hh568670.aspx. Sentinet fully supports these configurations and Sentinet Node's web.config file can be configured with this section, for example:
<trustedIssuers>
<add name="My STS"
thumbprint="20139F2D80D1493ECDC5E66ED712F1723FEA7701" />
</trustedIssuers>
When <trustedIssuers> section is configured with named trusted issuers, the name attribute value will be used to generate claim issuer's name claim. That name value can be then used in the Sentinet Claim Access Rule Expression instead of the digital thumbprint value.
Sentinet further simplifies configuration of the Named Trusted Issuers and provides a User Interface to configure them remotely from the Sentinet Administrative Console. The latter approach eliminates the need to modify Sentinet Node's web.config file manually and allows management of the Trusted Issuers dynamically and remotely.
To add Trusted Named Issuer to a Sentinet Node click + Add button.
In the Add Trusted Issuer Identity dialog box provide Issuer Name (user friendly issuer name) and select the option of how the Issuer certificate will be provided:
Specify certificate thumbprint
Upload public part of the certificate.
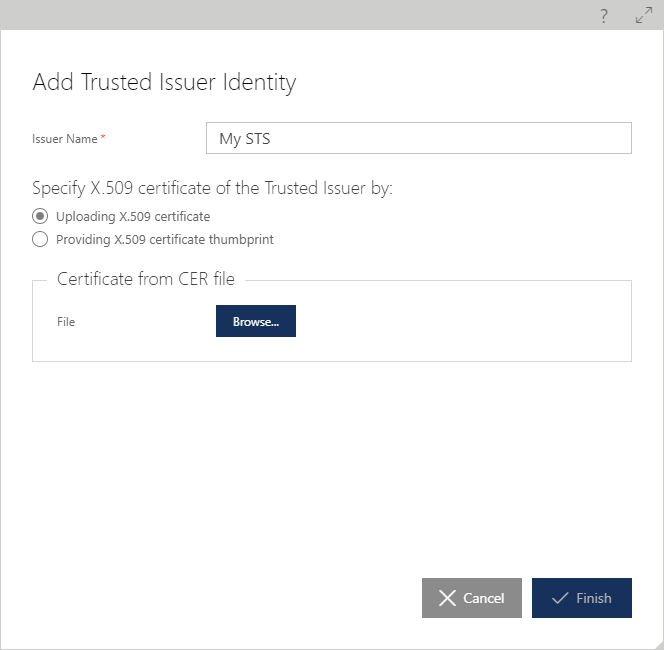
There is no significant difference between the two options. Some STS servers do not provide complete public part of their signing certificates, so option 1 might be the only option. On the other hand, and from a Governance perspective, it is always advisable to provide complete public part of the certificate (when it is available), so that the Sentinet Repository can be used to retrieve this certificate at any time and to monitor its expiration.
